
The Security Accounts Manager (SAM) in Windows
Dive into the Security Accounts Manager (SAM) in Windows
Hi everyone, 👋
Today, I’ll review the Security Accounts Manager (SAM), a key component of the Windows operating system’s security infrastructure. SAM is responsible for managing user accounts and their associated credentials. It maintains a secure database in the \Windows\System32\config directory that stores critical information such as usernames and password hashes.
Functionality of SAM in Windows
SAM’s primary role is facilitating user logins by authenticating credentials against its database. When a user attempts to log into a system, the credentials entered are verified against the information stored in the SAM database. If the credentials match, access is granted; otherwise, an error message prompts the user to re-enter their credentials.
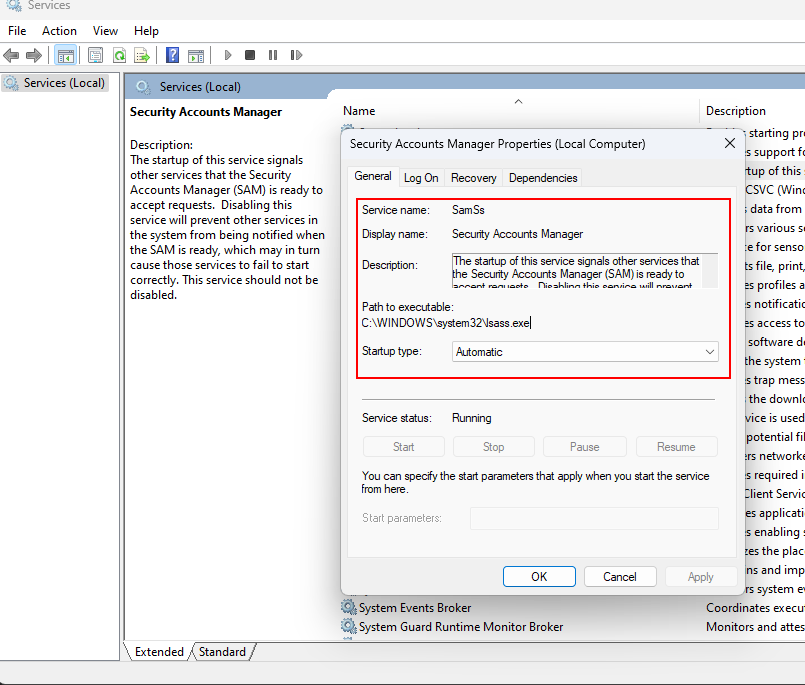
SAM in Active Directory
In the context of Active Directory (AD), the Security Accounts Manager extends its functionality to manage network-wide user accounts. Two significant fields within AD SAM are the sAMAccountName and the userPrincipalName (UPN). The sAMAccountName, limited to 20 characters, is a legacy identifier used for backward compatibility, following the format domainname\username. In contrast, the UPN serves as a modern login name resembling an email address without a character limit and is often formatted as username@domainname.com.
Evolution of SAM
The SAM database originally utilized LAN Manager (LM) hash or New Technology LAN Manager (NTLM) hash formats to store passwords. The LM hash, however, had significant security weaknesses, prompting the adoption of the more secure NTLM hash. NTLM uses the MD4 algorithm and supports both uppercase and lowercase letters, providing stronger security. To further enhance security, Microsoft introduced the SYSKEY function in Windows NT 4.0, which encrypts the password hash values in the SAM database, mitigating the risk of offline attacks.
How SAM Functions in Different Environments
On Local Computers
On a standalone local computer, SAM’s primary role is to store and verify the password of a single user. The SAM file operates in the background, facilitating secure access to the system. It’s worth noting that SAM database backups, which are used for recovery purposes, can sometimes be accessed without specialized software, posing a potential security risk.
In Local Area Networks (LAN)
Within a LAN environment, particularly when managing Active Directory users, SAM is crucial in verifying both local and network passwords. When a user logs in, Windows prompts for credentials and verifies them against the SAM database. Successful verification grants the user access to the network, while failure denies access, maintaining network security integrity.
SAM Vulnerabilities
SAM: HKLMSAM
Windows’s Security Account Manager (SAM) database stores user account information, including usernames and hashed passwords. This data is for authenticating users during login attempts. The hash complexity depends on the encryption algorithm, including the older DES-based LM (Lan Manager) encryption or the more modern NTLMv1 and NTLMv2 algorithms. Both NTLM versions produce a 32-character hexadecimal hash derived from the MD4 digest.
A common method of obtaining these hashed passwords is to dump the SAM database. This can be done using specialized tools that extract password hashes or by copying the registry data to a file (e.g., reg.exe save hklmSAM) for offline analysis. Once obtained, these hashes can be subjected to brute-force attacks to discover the actual passwords.
LSA Secrets: HKLMSecurity
The Local Security Authority (LSA) in Windows manages a system’s local security policy and stores sensitive information, known as LSA secrets, in the registry. These secrets include various types of data, such as:
- User passwords
- Internet Explorer passwords
- Service account passwords
- Cached domain password encryption keys
- SQL passwords
- SYSTEM account passwords
- Passwords for scheduled tasks
- Information related to the activation status of Windows
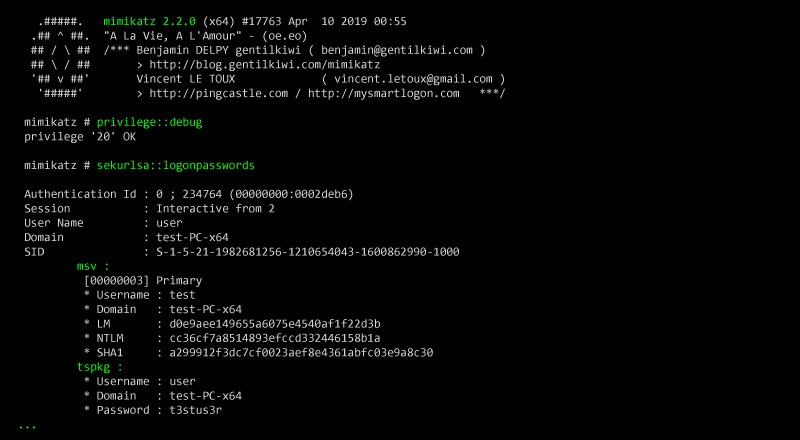
Mimikatz
Access to LSA secrets is restricted to SYSTEM account processes. Despite these protections, tools like Mimikatz can extract LSA secrets from memory and registry hives on specific Windows versions.
SYSKEY: HKLMSystem
Syskey, also known as the SAM Lock Tool, was a feature in older Windows versions designed to encrypt the SAM database for additional security during system startup. Syskey protected this sensitive data while the operating system was not running. Once the OS started, the Syskey value was loaded into memory, allowing the SAM to be decrypted.
Although the Syskey feature was discontinued in 2017, it can still be found in the registry under hklmsystem on older Windows versions where it is enabled.
- SeriousSam (Hive Nightmare): This vulnerability affects Windows 10 and 11, allowing attackers with user-level access to execute Pass-the-Hash attacks, potentially accessing hashed passwords stored in SAM and the Registry.
- sAMAccountName Spoofing (CVE-2021-42278): This vulnerability, with a severity rating of 7.5, relates to a privilege flaw in the Active Directory Domain Services (AD DS) component, which could be exploited to gain elevated privileges.
- SAMR (Security Account Manager Remote) Vulnerability: This vulnerability could enable attackers to bypass security features by matching passwords with usernames through multiple attempts.
- SAM and LSAD Protocol Vulnerability: A flaw in the SAM and Local Security Authority (Domain Policy) (LSAD) remote protocols can provide attackers with elevated privileges and access to the SAM database.
The Importance of Hardening SAM
Given the critical role and vulnerabilities of SAM, hardening this component is essential for system security. A robust server security policy, especially for domain controllers, is vital. Organizations are encouraged to follow security baselines, such as those recommended by the Center for Internet Security (CIS) and the National Institute of Standards and Technology (NIST). Key recommendations include:
- Restricting Remote Calls to SAM: Limiting the number of clients who can make remote calls to SAM reduces the risk of unauthorized access.
- Preventing Anonymous Enumeration: Blocking anonymous users from listing SAM accounts and shares prevents attackers from gathering information for social engineering or brute-force attacks.
For organizations lacking the time or resources to implement these measures manually, Zero-Defense Labs offers comprehensive solutions. Our services include system hardening and ongoing security management to ensure your SAM and other critical components are secure.
References:
https://support.microsoft.com/en-us/topic/kb5008102-active-directory-security-accounts-manager-hardening-changes-cve-2021-42278-5975b463-4c95-45e1-831a-d120004e258e
https://www.trendmicro.com/vinfo/us/threat-encyclopedia/vulnerability/3218/ms14016-vulnerability-in-security-account-manager-remote-samr-protocol-could-allow-security-feature-bypass-2934418
https://github.com/gentilkiwi/mimikatz
Contact us to learn more about how we can help protect your systems from vulnerabilities and attacks.
More Articles
Continue reading about cybersecurity

